No car is an island as fleets abound in the brave new world of connected vehicles
You might be shopping for a new car, but it won’t be a discrete one as in the past. It will be a fleet member. Same for trucks, buses, tractors motorcycles and just about every type of vehicle.
As of 2020, 98% of new cars have internet connectivity as compared to only 35% as of 2015. The modern telemetry units are in constant contact with the internet. Inside, they host a plethora of interfaces that generate large amounts of data. In-vehicle we see wired and wireless (Bluetooth, Wi-Fi) communications and latch onto 4G/5G cellular networks either from an embedded mobile phone or via a connection to the smartphone that you carry around.
The global connected car market is expected to double in the next five years with more than 270 million of such cars to be shipped during 2020-2025, according to the latest research from Counterpoint’s Smart Automotive service.
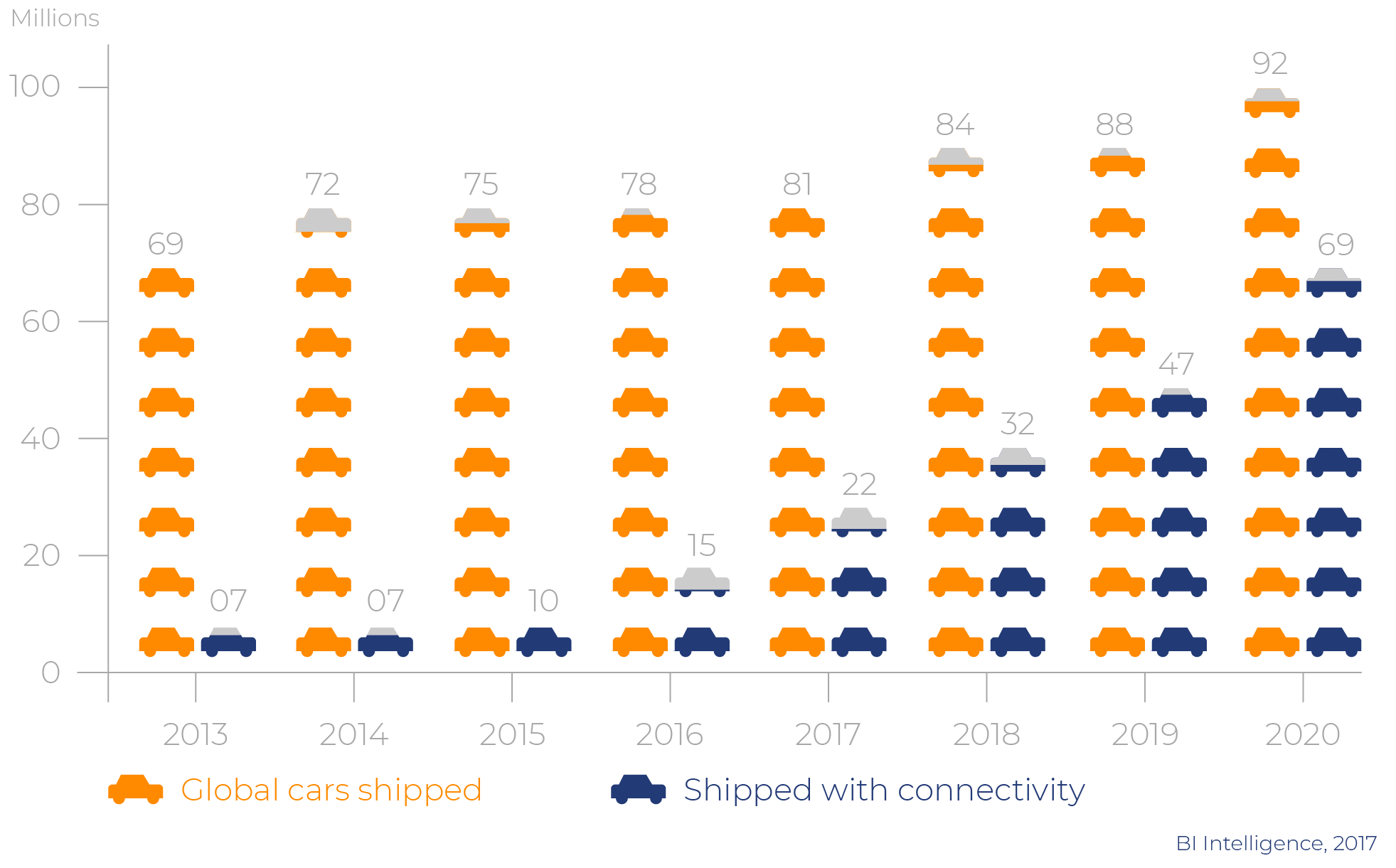
It’s important to note that “connectivity” doesn’t just mean “constant communications”. It also means that your new car will be a member of one, and probably several, fleets simultaneously.
How so?
Carmakers want to know how each of their cars is behaving. 100+ embedded electronic control units and several secure data stores are recording performance, usage and other data in real-time and periodically uploading gigabytes to the manufacturer’s data center for analysis. The carmaker looks across the entire population of the car model on the road as a fleet from which vast volumes of data are pouring into a big-data analysis engine, or even several engines, for a wide variety of purposes.
But the carmaker isn’t the only fleet manager. Insurance companies wants to know how each insured driver uses the car. The connected car goes a lot farther than merely answering the standard insurance questions: “Have you had any accidents in the last three years?” and “What are your drinking habits?” The insurance company can now find out how often insured drivers fills the tires, if they are hard on the brakes, and even how often they switch lanes. The millions of insured drivers constitute another sort of a fleet.
The dealership that sold the car and the service center that maintains the warranty are other types of fleets. They want accurate predictive maintenance to know when the next checkup should be scheduled or perhaps are in need of other advanced fleet maintenance functions. The cars they have sold will automatically let them know when it’s time for maintenance along with any problems since the last checkup.
Trucks, buses, taxis, rental cars, limousines and other commercial vehicles (think UPS) are often members of traditional fleets. Today, those fleets can also include car-sharing—a kind of rent-a-car-by-the-hour—as well. Uber and Lyft maintain fleets, but not in the traditional sense. Their fleets consist of private cars that participate in the peer-to-peer ride-sharing service.
With the plethora of operational data automatically feeding fleet management systems, dealers can offer attractive discount programs to commercial fleet buyers even for small fleets of fewer than 10 cars. In fact, some dealers can provide a fleet registration number even if a company leases only a few cars. So, the company car is a member of still another fleet.
Banks are getting in on the action as well. With all this actual performance data available, they can offer accurate financing tuned to the size and use of the fleet no matter what the size. The banks now look on these cars as their own fleet.
Fleets abound and just about every vehicle will be participating in one, or several, in some capacity.
Cyber Security and the Fleet
Advanced fleet management depends on the constant flow of accurate data directly from the vehicles to the fleet manager’s data center.
To thwart cyberattacks and ensure protection of the fleet from vehicle hacking, data must be maintained securely while at rest within the vehicle and while in transit from the vehicle to the fleet data center and from the data center to the vehicle.
Our study of the automotive industry and cybersecurity trends indicates that singular vehicle attacks may soon be a thing of the past. Fleetwide attacks - which will have a much more significant scope and impacts as well as a much greater payoff for cyberattackers - threaten to disrupt not only automotive security but also many other aspects of the automotive business and operating model.
Gary Silbert - National Automotive Leader, KPMG
A successful vehicle hacking attack on the fleet could result in:
- Loss of command and control communication with vehicles
- Interruption in incoming data from vehicles
- Inability to access location data for route planning
- Termination of data services
- Cessation of emergency services
- Inability to send OTA updates to vehicles
Data at Rest
Every day, gigabytes of data are collected within the vehicle and periodically uploaded. As the vehicle accumulates telemetry and other data, it must be retained securely, with absolute protection of its privacy and integrity.
Deleting the data would devastate many fleet management tasks. Falsifying the data could be worse, leading to erroneous analysis of performance and other indicators. Inappropriate access to the personal information stored in the vehicle, such as phone numbers, address books, credit card details and location information, could be misused directly or exploited for blackmail. Loss or misuse of this data could also result in severe non-compliance penalties with regulations such as GDPR.
Proprietary manufacturer, service provider and app vendor data obtained from vehicle head units can wreak havoc in the wrong hands. Once hackers gain access to personal and other information from car systems, they are certain to find “interesting” ways to use it. GPS information can be used to track a driver’s personal habits and schedule to plan a burglary when a driver is away from home. It can also be used in a social engineering attack by sending a seemingly innocent email saying: “You left this at the mall” with a link to malware instead of a photo.
There are many other attack vectors that target fleet vehicles. Hacked aftermarket parts can be used to steal or falsify valuable data. USBs carrying new apps or updates ostensibly from the manufacturer, service provider or app store can open vulnerabilities for vehicle hacking on a fleet-wide scale.
Data in Transit
In transit, data can be intercepted and misused just like data at rest. However, the potential for malicious activity is far greater. The many communication channels within the vehicle as well as from/to the vehicle pose numerous ways for hackers to intercept transmissions including:
- Cellular phone systems
- GPS
- Radio
- LiDAR
- Optics
- Wireless sensors
- Dedicated Short-Range Communications (DSRC)
- Near Field Communication (NFC)
- Bluetooth Low Energy (BLE)
- Wi-Fi
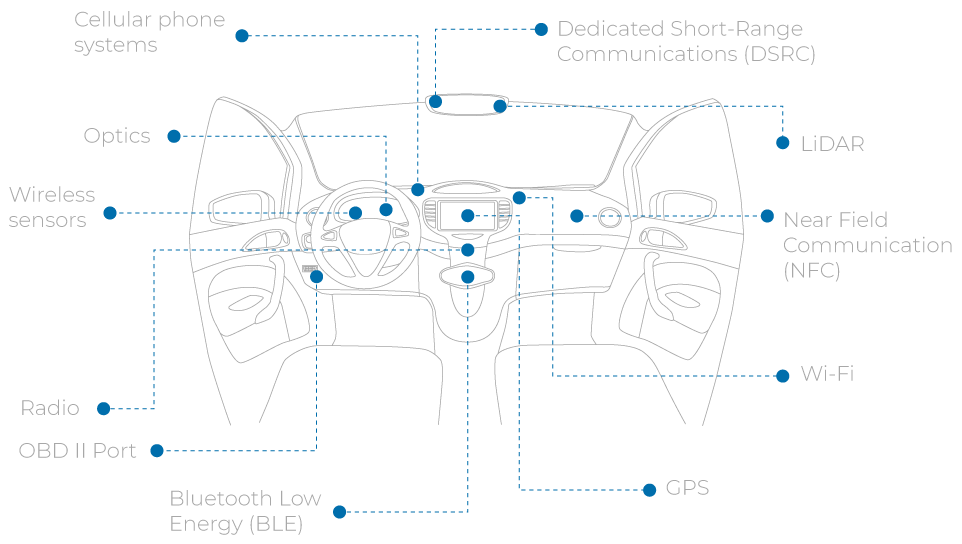
Most of these communications channels are beyond the reach of the car manufacturer or fleet operator. A nefarious Wi-Fi listening device will almost certainly find its way into the hands of fleet hackers.
In addition to the integrity of the transmitted data itself, connected components in the fleet ecosystem need to be authenticated to be sure that communication comes from trusted sources. The vehicle needs to ascertain that OTA updates or updates obtained at a service center are the real thing. The data center needs to know that the vehicle data actually came from the vehicle, otherwise, man-in-the-middle attacks, pervasive in the IT world, are bound to visit fleet management systems.
We’re All in This Together
While every vehicle must be seen as another endpoint to be secured, fleet membership has its own “rewards”. There is an enormous opportunity for sophisticated hackers to use the vehicle as a backdoor to gain entry into fleet management and other business systems. Therefore, all data in the vehicle and transmitted between the vehicle and the fleet management system must maintain an impenetrable barrier to cyberattack and misuse.
The GuardKnox product family is the foundation for secure hosting of dynamic capabilities and services in the connected car and fleets. GuardKnox products serve as an in-vehicle endpoint for the automotive industry “app-store”, locking down and securing:
- In-vehicle data as it is collected and stored
- ECU communications
- Wireless connections with aftermarket accessories
- Telematics
- Infotainment
- OBD port
The GuardKnox Aftermarket Add-On is an especially attractive aftermarket solution, fitting seamlessly into the automotive value chain without requiring any third-party integration. It is easily retrofitted in the maintenance garage--it’s just a simple plug-in install in the OBD port and can be installed at any point in the vehicle lifecycle.
The Key Advantages of the GuardKnox Lockdown Communication™ and Aftermarket Add-On for Fleets:
- Fends off cyber-attacks: Ensures that the vehicle functions as designed.
- Fully deterministic: No learning systems, statistical mechanisms or heuristics required. No false positives.
- Stand-alone operation: No need for constant updates nor re-configurations.
- Free of constant communication: No ongoing cloud connectivity necessary.
- Seamless integration: Simply plug and go
- Full support for secure over-the-air (OTA) updating – adding functionality to vehicles on the road
- Helps streamline operations, inventory management and provides vital fleet analytics for advanced fleet maintenance







