Protecting Your Electric Vehicle From the Danger of EV Charging Networks
March 21, 2019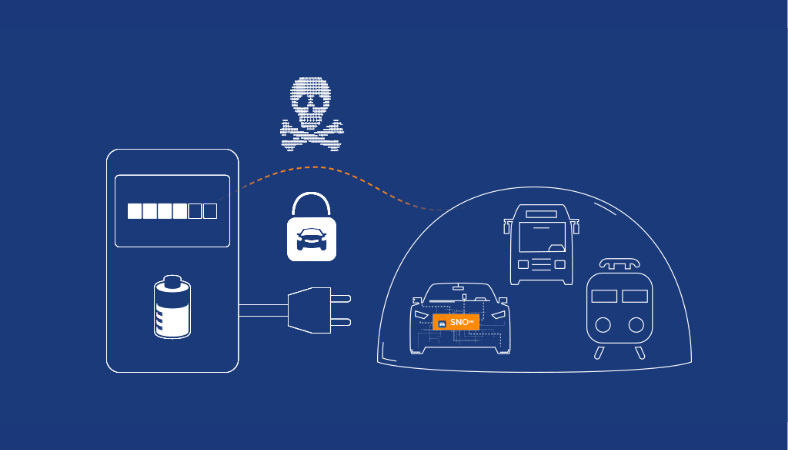
The third of three blogs about securing the EV market.
Taking "Connected Cars" to the Next Level
With the publicity surrounding the cyber-hijacking of a Jeep in 2015 and the numerous articles about the rash of keyless Tesla thefts in 2018, the cyber risks of connected cars are just beginning to enter the mainstream consciousness. There is significant appreciation that the computer-driven conveniences of modern cars have turned them into computer-on-wheels, with all of the cyber risks that are common to computer networks and smart phones.
But most have yet to internalize that electric vehicles are taking the dangers of connectivity to entirely new levels. The recharging process opens a highway for unprotected messages between your vehicle and a charging station, potentially giving viruses and hackers unfettered access to your car’s computer networks through a variety of protocols. These risks are compounded by the increasing use of public Level 3 charging stations that can be physically accessed by cyber criminals and or inflected by other unprotected EVs.
The Vulnerabilities of Vehicle-to-Grid (V2G) Communications
The EV charging process is guided by two standards for communication: The Open Charge Point Protocol (OCPP) that allows charging stations to communicate with backend systems and the ISO 15118 standard for bidirectional vehicle-to-grid communications.
The V2G communications between the vehicle and EV charging networks, with its direct access to the vehicle network is the primary risk to electronic vehicles. In addition, it is composed of a number of well-known protocol suites with equally well-known risks:
- The XML protocol is prone to denial-of-service (DoS) attacks, data theft and remote code execution (RCE)
- The TCP/IP protocol can be hacked through number spoofing, routing attacks, source address spoofing, and authentication attacks
- TLS ostensibly used to encrypt data has been proven to be easy to hack
- PLC (Power Line Communications) protocol can be physically intercepted and decrypted
A Cybersecurity Solution Designed to Protect EV Charging Networks
The EV ECU for electric vehicles is uniquely suitable for protecting EVs from the threats posed by vehicle-to-grid (V2G) communications by
- Examining all Vehicle-to-Grid communication to and from the EV.
- Managing and monitoring the grid charging procedure.
- Maintaining and ensuring the safety of charging operation.
- Enforcing and ensuring the security of sensitive data and in the -vehicle network from all current and future external threats.
The solution architecture is split into an external partition and an internal partition. The external partition handles all external communication with the vehicle. Using GuardKnox’s patented three-layer Communication Lockdown™ methodology, GuardKnox examines all messages on the routing layer, the content layer and the contextual layer.
Only allowed “legal” communication such as PLC, CAN or wireless communication is permitted to cross to the internal partition, while all unauthorized or improper communication is dropped, including communication from the EV charging network. In addition, all protocol-related data is stripped out to prevent protocol-level attacks as GuardKnox mediates the data-stream between the external environment and the internal partition. Once data has crossed to the internal partition, GuardKnox examines the content and context of all communications for safety before passing the data to the internal vehicle network.
Unique End-to-End Architecture that Meets your Current and Future Needs
The software of the GuardKnox cybersecurity solution is supported by end-to-end hardware architecture that is designed to meet the dynamic needs of EVs. The hardware design is flexible, allowing multiple operating systems to run in parallel on the same chip. This allows the current and future consolidation of applications onto a single ECU, while supporting the hardware and software separation between safety critical and non-safety critical applications for improved protection against EV charging threats and other automotive cyberthreats that aim to infiltrate non-safety critical applications as a ‘stepping-stone’ to access safety critical systems. (As well as threats that target non-safety critical systems as their ultimate goal.)
The architecture also supports multiple industry standard interfaces in hardware (implemented on the chip) with the scalability to add new or upgraded interfaces to the design without changing the chip. This is especially important since the EV and EV charging markets are in their early stages of growth and many standards are still in development.
The Bottom Line
The EV charging network and ecosystem is still relatively new and continues to rapidly evolve. Connecting to charging systems—especially public charging systems—opens connected vehicles to a whole new set of cyberthreats at the network, protocol and content levels. In such a dynamic environment, reactive solutions such as intrusion detection/intrusion protection systems (IDS/IPS) cannot offer real-time protection and will require constant updates as the ecosystem changes.
Only the GuardKnox EV ECU for electric vehicles offers a hardware-software solution with a deterministic approach in which all traffic is analyzed at the routing, content and contextual layers. Since all “legal” traffic is predefined, this ensures that:
- Only relevant data is exchanged with the appropriate parties on the EV charging network (e.g., credit card data with an eMSP)
- Inappropriate requests are rejected (e.g. messages from the EVSE to the drivetrain or vehicle safety systems)
- The electric vehicle is fully protected from current and future threats without the need to update the software