This blog was updated in July 2021
Vehicles today are defined by their software, but are they designed for the complexity and challenges associated with their software? With so much connectivity on the road, vehicles must be secure by design just like laptops and desktops on a private network.
With over 100 ECUs in each vehicle and 100s of millions of lines of code, the overwhelming amount of software can cause engineers to spend weeks trying to find a single bug that is compromising or damaging vehicle safety, performance, and/or functionality.
Some of the greatest advances in vehicle connectivity are quickly becoming the biggest threats to automotive cybersecurity and the traditional IT cybersecurity methods will just not cut it.
Connected Vehicle Ecosystem
If we compare vehicles to traditional IT networks, each vehicle is a virtual local area network with numerous endpoints (every ECU can be considered an endpoint). Just like IT local area networks and endpoints, they are subject to cyberattacks.
Manufacturers must implement powerful automotive cybersecurity mechanisms even more extensive than those used for IT cybersecurity. Approaches used for IT cybersecurity are relevant for certain subsystems of a connected vehicle, but for others a vehicle-specific approach to connected car data and safety protection is required.
The connected vehicle ecosystem can be split into five interlinked subsystems:
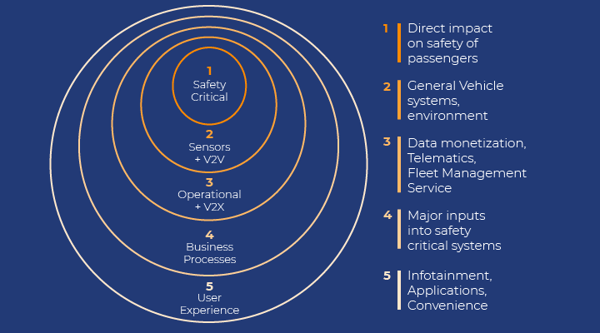
- Safety critical subsystem (powertrain components) with direct impact on the safety of vehicle passengers and others
- Sensors and V2V Communication provides major inputs to the safety critical subsystem
- Operational and V2X Communication includes general and non-critical, safety subsystems and vehicle environment-control components
- Business Processes include components related to data monetization as well as Telematics and Fleet Management System (FMS)
- User experience (UE) includes infotainment, apps, and convenience components
What is Automotive Cybersecurity
So what is automotive cybersecurity and what makes it different from IT security?
The connected vehicle requires enormous processing power, vast data storage and numerous communication channels. Virtually all of the vehicle’s functional subsystems participate in the layered network shown above and all of them have been subject to attacks by white-hat and black-hat hackers.
Traditional IPS and IDS technologies provide adequate safeguards and reporting for the non-safety-related, open subsystems in layers 3-5 and depend on heuristics, machine learning and other reactive methods to identify and deal with attacks.
However, as we move to Safety-Critical operations in layers 1 & 2, connected cars must be maintained as closed systems with a deterministic capability that is preventative as opposed to reactive. It is after all, a matter of life and death!
Cyber attacks against safety critical subsystems
While losing use of the radio or suffering data leakage, while unpleasant or somewhat damaging, do not endanger the safety of passengers. However, the same cannot be said for layer 1 & 2 Sensors and V2V Communication as well as all Safety Critical functions. Here, we need perfect, deterministic cybersecurity in real-time.
Relevant sensors and gateways include:
- V2V/VI gateway
- RADAR sensor
- LIDAR sensor
- Camera(s) sensor
- Ultrasound sensor
Safety Critical Subsystems include:
- Brake, throttle, steering and ignition key
- Airbags
- Advanced Driver Assistant System computer and sensors
- Anti-lock Braking System
- Electronic Stability Program/Subsystem
In this case, we are ultimately concerned with the kinds of attacks that can endanger life and property and which explains the importance of automotive cybersecurity:
- V2V/V2I gateway authentication, integrity and denial of service
- Sensor validation and security, authentication and jamming of RF signals
- Malware gaining control over a safety-critical ECU
- Malware taking control over the communication to the ECU or component
- Communication disruption (Denial of Service) over a critical segment of the CAN bus
- Omission in the supply chain where an original component is replaced by a malware-infected part
- Flaw in the software/firmware management where the original software/firmware component is replaced with a malware-infected counterpart
Deterministic Automotive Cybersecurity
A deterministic approach to cybersecurity at the Safety Critical level is mandatory for passenger and vehicle safety. Here, we cannot rely on the post-event remediation methods of IT cybersecurity. False positives and false negatives are not an option when lives are on the line.
The components of the Safety Critical Subsystem play a crucial role in preserving the safety of the vehicle, its driver and passengers. In this case, implementation of the cybersecurity solution has to comply with very strict requirements as our lives depend on it:
- A deterministic and reliable mechanism that is verifiable and certifiable, and that can detect and prevent the cyber threat in real time (preferably in hardware). Software solutions that require post-event analysis by security experts or that are prone to false positives are inadequate.
- Formally documented and certified “safe” for the vehicle driver and passengers for each hardware/software/firmware new version—including its embedded cybersecurity component.
- Mandatory extension of OEM and Tier1 product-qualification procedures as well as production-verification and validation procedures to include the cybersecurity component so as to prevent rogue hardware and software/firmware components from creeping into the supply chain via the production line and at maintenance sites.
- Download of new versions of software/firmware must be performed using encrypted object-code images signed with electronic signatures that can be verified against the data in the OEM depository. The download of object-code images with incorrect electronic signature must be blocked.
Secure by Design
Driver preferences and desires have changed dramatically. Consumers want customized experiences and the industry is adapting to answer those needs. Increased personalization and connectivity mean more software, but that does not need to mean greater vulnerability.
Deterministic security (or secure by design) demands that all potential operating permutations must be modeled comprehensively and that any communication or process execution is unable to take the subsystem out of the realm of acceptable behavior. The security mechanism’s threat-agnosticism means that attacks of any type (foreseen or not) and from any source cannot compromise any safety-critical ECU or communication.
Secure by design vehicles enable OEMs to provide an advanced driver experience without compromising on automotive cybersecurity.
GuardKnox’s deterministic cybersecurity methodology, Communication Lockdown™, answers the requirements of the Safety Critical Subsystem for the connected car. Its fully deterministic, closed-system approach does not look for attacks but ensures that the vehicle continues to function as it was designed. The security design has no need for cloud connectivity nor for ongoing updates so no malware can sneak in and corrupt the safety requirements of the vehicle.






