Automotive Cyber Security Essentials and IDS IPS Technology for Vehicles
February 11, 2018
What You Need to Know
Since the 1990s, networks, computers and data have come under cyberattack in countless ways. Entire companies and departments (under names like Security Operations Center, Incident Response Team, CERT, CSERT, etc.) have sprouted up to deal with the rapidly expanding challenge of protecting the digital assets of enterprises and individuals.
As the automotive vehicle becomes more digitized and connected, it joins this cybersecurity ecosystem while introducing its own, unique attack vectors and vital protections. In this blog, we discuss the ways that Information Technology (IT) departments (our collective name for those responsible for cybersecurity in the enterprise), charged with maintaining systems that interface with the internet, implement open system solutions as automotive cybersecurity essentials to the growing menace of cyberattack.
In our blog about Traditional IT Cyber Security technology vs. Automotive Cyber Security explained, we delved into where IT cyber security solutions can and should be applied to the connected car and where they are a dangerous mismatch. Recognizing that the needs of a closed system like the connected car are significantly different, automakers dare not implement IT cyber solutions in the safety-related areas of their vehicles. That is why automotive cyber security requires an entirely different mitigation plan.
It is crucial to recognize that within a vehicle, there is a close group of messages while within a traditional computer there could be an almost infinite number of messages going back and forth simultaneously. Therefore, any security method which employs statistics is not accurate enough to defend a moving platform - this is true for fighter jet systems and the same principle applies to vehicles as well.
IPS/IDS Methodologies
In the traditional open/exposed IT network, a first line of defense will include Intrusion Prevention Systems (IPS) designed to keep hackers and malicious exploits out.
As IT and cybersecurity professionals know too well, no IPS can hermetically seal the exposed network and all of its hardware and software. There are far too many entry points and opportunities for lateral movement. So, the CISO and cybersecurity staff also deploy a litany of Intrusion Detection Systems (IDS) to identify cybersecurity threats. Usually residing on endpoints and servers, IDS constitutes a group of security-related software systems (anti-virus, firewall, etc.) designed to identify and alert security administrators when someone or something has tried or is trying to compromise information or operation with malicious activities or through security-policy violations.
Where Post-Incident Response is Not an Option
Traditional IT cybersecurity measures are reactive, often discovering and reporting on events that have already happened. In the open system world of the IT network, IDS/IPS approaches are not able to stop all attacks. In fact, they fail routinely.
As heuristic systems that learn as they work, IDS/IPS solutions are in constant need of threat-intelligence updates. Always a step behind the latest hack attacks, they can achieve only, at best, a 98% reliability rate. This level is impressive in the IT context but is completely unacceptable for operating a vehicle. You can tolerate the automatic identification and mitigation of 98% of cyber attacks on your data, reacting quickly to actual incidents, but would you ever drive a vehicle whose brakes work only 98% of the time? Would you allow your family to ride in a vehicle whose safety-critical systems are only 98% reliable? In addition, IDS/IPS generate ‘false positives’ which is a completely unacceptable for the security levels of a moving vehicle.
How IDS/IPS Threat-Mitigation Works
The IPS monitors the network for malicious activities such as security threats or policy violations. Placed in the direct communication path between source and destination, the IPS analyzes and takes action on all undesired traffic flows that enter the network. Upon spotting a possible threat, the IPS will:
- Generate an alert for security analysts
- Drop malicious packets
- Block traffic
- Reset connections
The IDS identifies and alerts security analysts when it detects malicious activities or security-policy violations. It employs several methods such as signature-based detection where a pattern or file signature is compared to a gigantic and incessantly growing database of known threats.
This method is useful for finding already-known threats, but does not help in finding new threats or variants of threats. Thus, there is a need for consistent updates in order for IDS defenses to be viable. If the IDS is out-of-date or is not able to communicate with the database, its veracity in detecting threats is heavily undermined. Some IDS employ anomaly-based detection which compares the definition or traits of a normal action against characteristics marking the event as abnormal. Here, too, a dynamic database must be established and maintained.
In their enthusiasm for blocking multitudes of possible cyberattacks, IDS/IPS solutions are known for generating multitudes of ‘false positives’—events that are considered suspicious but are, in fact, harmless. To the chagrin of cybersecurity personnel, even the best IDS and IPS systems incorrectly report more than 9% false positives. But even a 1% rate is unacceptable in a moving vehicle’s safety systems. There is zero tolerance for a false report of brake failure. This is not just cybersecurity; this is the difference between life and death!
Scope of Cyber Attacks in the IT World
Cyber attacks on open systems take many forms. They target all of the components of the modern IT structure:
- Network
- Endpoints
- Servers
- Data
- Communications
- Internet
- Cloud
- Devices (computers, mobile phones, IoT, etc.)
The following table surveys the main cyber techniques that hackers use to invade IT networks and systems and which do harm more than a million times a day. New cyber techniques are being invented all the time.
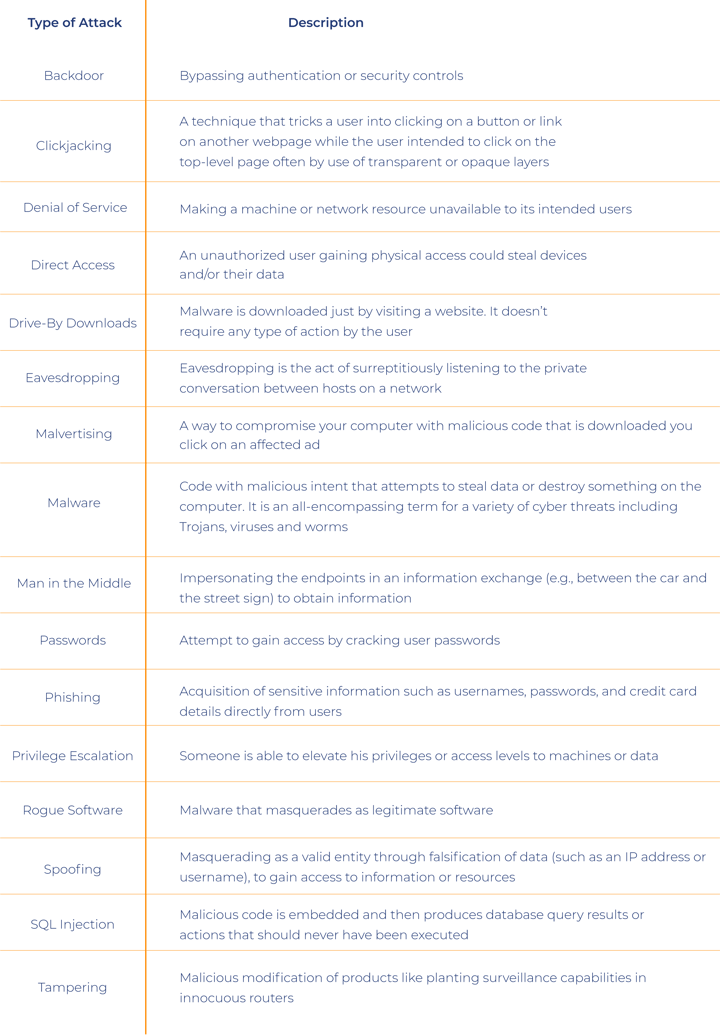
As every network is different, there is no one-size-fits-all approach to cybersecurity. The more links in the network chain, the more opportunity for hackers to penetrate. Every network requires skilled professionals to plan, operate and defend all fronts against cyberattacks: apps, databases, endpoints, network devices, cloud servers, communications, physical access, and the users themselves, the weakest link in the security chain.
Just as networks are complex organisms that grow and change over time, cybersecurity mechanisms must be monitored and adjusted as cyberattack vectors invariably mutate.
Effectiveness of IT IDS/IPS Technology for Automotive Cybersecurity Essentials
Regarding the connected car, non-safety-related issues like secure data storage, internet and external communications with the cloud, behave much like they do in the open-system IT world. They are subject to similar types of attacks and therefore respond to similar types of mitigation provided by IDS/IPS technologies. However, safety issues (in-car protection) with the closed-system vehicle cannot tolerate after-the-fact remediation nor false positives as they are the automotive cybersecurity essentials for safe travel. No fighter jet today relies on the IDS/IPS approach. In such closed systems, including the safety-related areas of the connected car, the security level must operate at 99.999% reliability; it demands a real-time deterministic approach, such as Communication Lockdown™ which complies to common criteria cybersecurity standards.





